How to create a good password 2025

We may earn a small fee from the companies mentioned in this post.
Almost every online service such as eBay, Hotmail, Facebook & Amazon require a static username and password as verification of your authenticity.
Whilst other techniques continue to be developed, including multi-factor security that can offer greater security (discussed later), the humble password is still widely accepted across the world due to its simplistic approach and familiarity. Password security is critical in safeguarding sensitive information from threat actors who exploit weak passwords.
It is therefore imperative you know how to create a good password to defend against brute force attacks.
What does a good password look like? Well, it can be described as the minimum complexity to ensure it is as difficult as possible for any potential cybercriminal to crack it. Brute forcing involves trying every possible combination of characters to gain unauthorised access, making it crucial to use long and complex passwords.

This article contains useful and constantly updated information that will help you understand the importance of using a strong password. It will show you how to develop a simple process to protect your online data.
If you wish to skip this information and jump to the ‘9 easy steps to create a good (secure) password’ – Click here
What is considered a secure password? To answer this question, you need to understand a little about how computers process a password and how the passwords are stored. When you type in a password, your computer verifies the specific characters you entered matches an internal list stored within the computer.
The process isn’t as simple as that described as it uses an encryption algorithm called a HASH to match what you type in plain text, to what is stored on the computer but the principle of checking what you enter on a keyboard against a known code is correct.
A computer will store a list of valid usernames and associated passwords for that system either locally or through a second computer system. This information is located within a database that can be referenced each time you log in that particular computer system.
As no computer system can be considered 100% secure, it is realistic to consider any computer can be hacked and therefore expose your username and passwords to cybercriminals.

To reduce this risk computers are designed to encrypt your passwords, so if a hacker gains unauthorised access to a computer and copies your credentials (username & password), the hacker will need to decrypt each password before they can compromise your account.
The complexity of a password can determine how long it takes a cybercriminal to decrypt or ‘crack’ an encrypted password. There are numerous methods used by cybercriminals to do this and it is important to have a basic understanding of these techniques, as they can help you chose an effective password that can make it difficult to ‘crack’.
Let’s imagine that one of your online email accounts such as Gmail has been compromised and your email address, which is stored unencrypted, copied along with its corresponding password that has been encrypted.
The cybercriminal will attempt to decrypt your password outside of the compromised Gmail computers, usually their own purpose build very powerful computers that can focus considerable processing power to decrypt your password as quick as possible.
Unlike your Gmail login, your compromised (copied) password won’t lock-out after 5 wrong attempts. The password lockout feature is embedded within the online application, not your password.
The cybercriminal therefore has unlimited attempts to crack your password. They will probably start with a ‘Dictionary attack’. This uses an extensive dictionary database of common passwords based on various languages and permutations.

The English language for example contains a vast number of words, the Oxford English Dictionary has more than 273,000 words, with around 171,476 in common use.
However, modern computing power using dedicated number crunching processors (developed for computer gaming purposes), are commonly used by cybercriminals as they can process up to 20 billion different passwords every second, using a pre-constructed dictionary list of words.
Dictionary and Brute Force Attacks
Dictionary password attack methods leverage a vast array of dictionary words and permutations, these can include first character uppercase and numbers at the end of the password, usually in date format. If you think back to my cyber security seminars, I discussed common passwords that can be easily cracked as they contain common dictionary-based names, these include: Oliver2003$ or James2020!

The process isn’t as simple as that described as it uses an encryption algorithm called a password hash to match what you type in plain text, to what is stored on the computer but the principle of checking what you enter on a keyboard against a known code is correct.
To overcome dictionary attacks, The National Cyber Security Centre amongst others have advocated the use of three random dictionary words to create a strong password, as this is considered harder to crack.
However, whilst it is true that a 3-word dictionary password can be considered more complex, and therefore theoretically more time consuming to break, there are flaws within this approach.
As mentioned previously there are 171,476 currently used words within the English language, however an average English native speaker knows approximately 20,000 words, with a university educated person knowing around 40,000 words.
Therefore, using the advice issued by the National Cyber Security Centre to incorporate 3 random words to construct a password, this would produce around 5,000,000, 000,000,000 – or 5,000 trillion different combinations of 3-word passwords. This is based on the 171,476 known words within the Oxford English dictionary.
Whilst this sounds a huge number for any cybercriminal to successfully attack, remember a modern powerful gaming computer can process up to 20 billion passwords a second. It would therefore theoretically take a suitably equipped computer as little as 4 days to crack a 3-word password.
In reality however, a 3-word password based on the most common 20,000 words known by an average person being attacked by the same computer could theoretically crack the password in less than an hour using a suitably constructed dictionary list.
The calculations above are based on single case letters. Using an uppercase letter for the first character of each dictionary word unfortunately makes little difference as the attack method assumes each word of the 3-word password is uppercase, which has no noticeable impact as it can predict this.

To make things more difficult for the cybercriminal you may wish to insert some random numbers and special characters into your password, but again these can be predicted by an enhanced dictionary attack method.
You may also replace some characters such as 0 (zero) for an ‘O’ or ‘3’ for an ‘e’. Modern password cracking software is aware of these tricks and has incorporated this into its attack process with little delay to the time it takes to compromise your password.
As a rule, try to avoid adding dates at the end of your password as these can easily be predicted. When a cybercriminal attempts to crack your password, they will use tools that are designed to reduce the work of the password cracking process with dramatic effect.
For example, a cybercriminal will assume that your password’s first letter will be uppercase and the rest lowercase as this is easier for an average person to remember. The cybercriminal will also assume any numbers will be semi-predictable and be at the end of the password.
What do I mean by semi-predictable? – Well, a date, usually within the past 80 years, but more likely to be in the last 20 years as this would represent the birthday of a child, or a pet. The date may also be a well-known one, like the year West Ham won the World Cup for England in 1966. Steer away from known dates as these will be incorporated within hacking tools when attacking your passwords.
You may also be required to add a special character to increase the complexity of a password. This is generally a very good idea but not if it’s at the end of the password and always: ‘!’ or a ‘$’. This action is expected and will be incorporated into the cracking software.
To further enhance security, systems should lock users out after multiple attempts with an incorrect password, as recommended by NIST guidelines.
Create a strong password examples
It is important you understand how to create a good password. For example, the password: BannanaWednesdayDog2009! – Can be considered strong but can be hacked within an acceptable timeframe. The first 3 words start with an upper-case character, this is followed by a recent date and an easy guessable special character. Using the same characters, a more complex version maybe: bAnnAna&wEDesdaydOg8520
However, constructing these types of complex combinations can be incredibly difficult to remember as the brain is not designed to compute in this way.
Pass-Phrase Passwords
You may also consider a pass-phrase, which is based on a sentence or statement. I have advised many people to use this technique over the years with great effect. For example: FortuneFavoursTheBrave , HeWhoDaresWins or OutOfThePark.

Unfortunately using a well-known passphrase can now be considered little better than using a dictionary based password as cracking software has a vast database of common phrases that can be used against an encrypted password. In some cases passphrases can be compromised quicker than using three random dictionary words described earlier.
Password Manager – Vault
To effectively defend against a dictionary or a passphrase attack it is important to create a strong password to protect your accounts, therefore forcing the attacker to use a brute force attack method as this can be very time consuming and potentially impractical.
A brute force attack attempts every possible permutation of every feasible character set when attacking an encrypted password. This method is by far the most difficult, time consuming and processor hungry way to attack your password and is usually the last resort for a cybercriminal.
The best passwords are those that are truly random in nature and cannot be guessed as they don’t conform to any language in any dictionary or phrase.
Unfortunately, truly effective complex random passwords are very difficult to remember which can be frustrating when you forget them. The easiest and most efficient way to remember these passwords is through the use of a secure password manager.
It is therefore important you consider using a good password generator, or secure password manager. A password manager or vault can create a randomly generated strong password, that is then encrypted and securely stored within the password manager application. An encrypted database within the password manager ensures that even if attackers gain access, they cannot easily decrypt the stored passwords, as highlighted by incidents like the LastPass breach. Deploying a password manager removes the need to remember passwords so they ‘can’ be very complex and near impossible for cybercriminals to decrypt.
A password manager can provide access to your online accounts effortlessly, without ever remembering the underlying password for any of your accounts. It can also ensure you do not use the same password across multiple accounts, which represents one of the biggest online cyber security risks.
Consider the table below which uses current computing power to estimate how long it will take to crack a truly random non-dictionary or passphrase password.
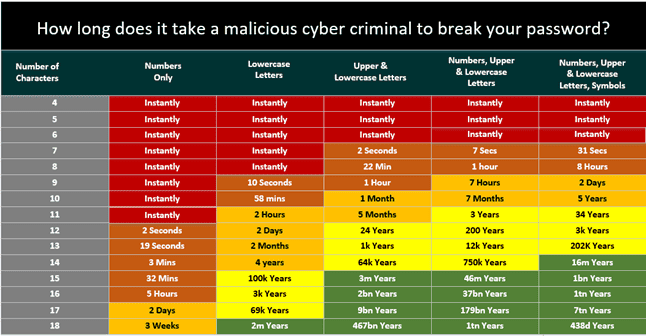
For more information, please see 7 Best Password Managers article that evaluates the best marketing leading Password Manager on the market in 2025.
Multi-Factor Security
When accessing more sensitive systems, such as online banking or remotely connecting to work desktops, it is highly recommended you use some form of Two-Factor Authentication (2FA).
Incorporating 2FA means that even if your password is compromised, a cybercriminal still can’t access your online account without your secondary authentication method, which can be a one-time code that changes every 30 seconds.
There are 5 common factors when authenticating to a computer system:
1. Something you know – Username, password
2. Something you have – A device that produces a random passcode via a mobile phone or security device
3. Something you are – Biometric (fingerprint, Iris or face recognition)
4. Where you are – Geo-Location data
5. Behaviour – Human behaviour patterns
Incorporating any two of more of these factors (multi-factor) is considered more secure than using a single factor method, such as username and password. Whenever possible you should consider using multi-factor security to access your most important online accounts.
9 easy steps to create a good password
By following these easy to adopt methods you will significantly reduce the risk of your online accounts being hacked and your data compromised.
1. Do not use dictionary words as passwords
As an example, don’t use weak passwords such as names of places like London, NewYork, or Paris. Do not use car names (Mercedes or Ferrari), or any item that would be listed within a dictionary.
2. Do not use dates within your password
Avoid using guessable dates, such as the birthday or a child, a pet or a memorable date in history such as 1066, 1966, 1767, 1666, or recent years such as 1950 – 2023.
3. Do not use sequential number or letters within your password
Numbers such as 123456, 123 or even 78910 can easily be guessed by attackers or auto build into automated password cracking software. Using sequential letters should also be avoided such as abcdef, zxcvb or qwerty (the last two examples being found on your keyboard).
As a general rule the longer your password is and the more complex, the harder it is to crack by a hacker. Whilst it is true you shouldn’t use dictionary words, combining 3 or more dictionary words is good practice, as long as you include random numbers and special characters. This makes it much easier to create and remember whilst difficult for hackers to attack due to the sheer number of combinations of 3 random words.
For example: TelevisionDoctorFootball226699£$ is considered a strong password. The Hive Systems Password Table is a valuable resource that illustrates how long it takes to crack different types of passwords, highlighting the importance of password length and complexity in ensuring security.
5. Use at least 12 characters in your passwords
The longer (and more complex) your password is the harder will be to crack, its as simple as that. Refer to the table that denotes the average time to break a password shown earlier in this article.
6. Do not reuse your password across multiple online accounts
One of the reasons so many accounts are hacked is due to individuals using the same password across multiple accounts. It is highly likely one of your accounts will get compromised at some point in the future. Hackers will often use compromised credentials across multiple online platforms as they know people use the same password multiple times. Never use the same password across multiple accounts, if you struggle remembering numerous passwords use a password manager (vault) to simplify things. Ensure you create a strong master password to securely access your password manager vault across various devices.
7. Never disclose your password to anyone
Absolutely never disclose your password to anyone. Remember banks, financial institutions or online businesses will never ask for your password. If they do it is highly likely that are fraudsters, however convincing they sound.
8. Use a Password Manager (Vault)
As mentioned previously it is difficult to remember numerous passwords. Using an industry recognised password manager (or vault) across all your devices will significantly reduce the risk of your online account being compromised.
There are numerous good quality Password Manager available – Click here to read my review of the best Password Managers
9. Use Multi-Factor (2-Factor) wherever possible
As mentioned previously deploying Multi-Factor can significantly reduce the risk of your account being hacked . Multi-Factor is something you know, have, are, or your location or how you login. Using 2 of these methods, usually something you know (password) and have (one-time code on your smart phone), can enhance your online security posture considerably.
Conclusion – How to create a good password
Whilst most people understand how to create a password, many fail to grasp the need to create a strong password, that is not used across different accounts.
Creating a good password is essential to protect your online accounts and personal data. A strong password should be at least 12 characters long, contain upper and lowercase letters, numbers, and symbols. It is also important not to use single dictionary words that can be easily cracked with hacking tools.
Avoid using information that can be easily guessed or obtained from public records such as birthdates, addresses, pet names, etc. It’s important to use different passwords for each of your online accounts so that if one account is compromised, the others remain secure.
Finally, make sure to change your passwords periodically to ensure maximum security. The use of Multi-Factor will provide an elevated level of security that makes it much more difficult to compromise.
FAQ
What is an example of a strong password?
When creating a strong password it should typically consist of a combination of uppercase and lowercase letters, numbers, and special characters. Here is an example of a strong password: R3$a!5tR0n8P@$$w0rd
What is the strongest password to use?
A strong password should meet the following criteria: – Be at least 15 characters long. – Include a combination of uppercase and lowercase letters, numbers, and special characters. – Avoid using common words or phrases. – Avoid using personal information such as your name, birthdate, or address.
Here is an example of a strong password: “bR4nDy!95$KeY
What is a good 8 digit password?
A 8-digit password can not be considered strong but by created by combining uppercase and lowercase letters, numbers, and special characters. Here’s an example: “M@k3Up1 it can be as strong as possible for a 8 digit password. Its better to choose a 12 digit password or 2FA instead
What is the 8 4 rule for creating strong passwords?
The 8 4 rule for creating strong passwords recommends using passwords that are at least 8 characters long and contain a combination of at least 4 different types of characters, such as uppercase letters, lowercase letters, numbers, and special characters. – This old rule has been sperceeded by the 12 4 rule
What is the 12 4 rule for creating strong passwords?
The 12 4 rule for creating strong passwords suggests using a minimum of 12 characters and including at least 4 different types of characters: uppercase letters, lowercase letters, numbers, and special characters.
A 12 digit strong password how long to crack it?
The time required to crack a 12-digit strong password depends on various factors such as the computational power used for cracking, the algorithm used, and the specific password cracking techniques employed. However, given the complexity and length of a strong 12-digit password, it can take a significant amount of time, potentially ranging from weeks to millions of years to crack it.
How do you create a strong password?
Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using personal information or common words. Make it at least 12 characters long.
How do I choose a good password?
Choosing a good password is crucial for online security, and following established password guidelines can significantly enhance your protection. Here are some guidelines to help you create a strong password:
Length and Complexity: Aim for at least 12-16 characters. Include a mix of uppercase and lowercase letters, numbers, and symbols. The more varied and longer your password, the harder it is to crack.
Avoid Predictable Patterns: Don’t use sequential characters (like 1234 or abcd) or easily guessable information (like your name, birthdate, or “password”).
Use a Passphrase: Consider using a random combination of words or an unusual phrase. This can be easier to remember and just as secure as a random string of characters, especially if it’s long.
Uniqueness: Each account should have its own password. Reusing passwords across multiple sites increases the risk if one site is compromised.
Avoid Dictionary Words: Passwords that contain common words or phrases can be vulnerable to dictionary attacks. If you use words, mix them with numbers and symbols.
Consider a Password Manager: These tools can generate and store complex passwords for you, so you don’t have to remember them all. They can also help you change passwords regularly.
Regular Changes and Updates: Change your passwords periodically, especially for sensitive accounts like email and banking.
Enable Two-Factor Authentication (2FA): Wherever possible, enable 2FA. This adds an extra layer of security by requiring a second form of verification beyond just your password.
Be Wary of Phishing Attempts: No matter how strong your password is, it can be compromised if you’re tricked into giving it away. Be cautious about where and to whom you provide your password.
Test Your Password: Use a reputable online password checker to evaluate the strength of your password. However, don’t input your actual password; use a similar example to test its strength. Remember, a strong password is just one part of good digital security practices. Always stay vigilant and informed about the best ways to protect your online information.
What is a strong 10 character password example?
A strong 10-character password should include a mix of uppercase and lowercase letters, numbers, and symbols to enhance security. Here’s an example: AB5b!7@Yz% Remember, it’s important not to use this exact password, as publicly shared examples can be more vulnerable. Always create a unique password for your own use.
Useful External Reference Sites
National Cyber Security Centre (NCSC)
Website: https://www.ncsc.gov.uk
Why it’s useful: The NCSC provides direct advice and support for the public and private sector in how to avoid computer security threats. Their guidance on password creation and management is grounded in the latest research and best practices.
Action Fraud
Website: https://www.actionfraud.police.uk
Why it’s useful: As the UK’s national reporting centre for fraud and cybercrime, Action Fraud offers advice on how to protect yourself online, including tips on creating strong passwords to prevent fraud.
Information Commissionaires Office
Website: https://ico.org.uk
Why it’s useful: The ICO is the UK’s independent authority set up to uphold information rights. Their site provides resources on data protection and has advice on creating secure passwords to help protect personal data.
With over three decades of experience in the heart of London’s financial sector, I have dedicated my career to the pursuit of robust cybersecurity practices and IT leadership. As a Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Chief Information Security Officer (C|CISO), Certified Ethical Hacker (CEH), and Computer Hacking Forensic Investigator (CHFI), I bring a wealth of knowledge and expertise to the table.
My journey in the field of cybersecurity has not only been about personal growth but also about sharing my insights with others. As an international speaker, I have had the privilege of addressing audiences worldwide, discussing the importance of cybersecurity in today’s digital age. My passion for knowledge sharing extends to my work as an author and blogger, where I delve into the complexities of cybersecurity, offering practical advice and thought leadership.
In my role as a CISO and Head of IT, I have overseen the development and implementation of comprehensive information security and IT strategies. My focus has always been on creating resilient systems capable of withstanding the evolving landscape of cyber threats.
My Master’s degree in Cybersecurity has provided a solid academic foundation, which, when combined with my practical experience, allows me to approach cybersecurity from a holistic perspective.
I am always open to connecting with other professionals in the field, sharing knowledge, and exploring new opportunities. Let’s secure the digital world together.

