Code Breaking – Deciphering the Intriguing History of Encryption

We may earn a small fee from the companies mentioned in this post.
Ever wondered how encrypted messages are decoded? Code breaking is more than a spy novel trope—it’s a craft that has influenced outcomes from Ancient Rome to cyberwarfare today. This guide takes you through the essentials of code breaking, celebrating its ingenious history, and examining its role in digital security and intelligence gathering.
Key Takeaways
Code-breaking, dating back to ancient times, has played a pivotal role in historical events, evolving from simple ciphers like the Caesar Shift to complex machines like the German Enigma cipher during World War II.
Significant breakthroughs in cryptanalysis, such as the work done by Room 40 during World War I and by Alan Turing and his team at Bletchley Park during World War II, not only influenced wartime outcomes but also laid the groundwork for modern computing and cryptography.
Despite the historical success in cryptanalysis, there remain unsolved codes like those in the Voynich Manuscript, and the field is constantly adapting to new challenges presented by advancements in technologies like artificial intelligence and quantum computing.
The Art of Decoding: Early Ciphers and Techniques

The art of decoding, or cryptanalysis, has a history as old as writing itself. Historically, ciphers have played a significant role in hiding sensitive and secret information, especially during warfare. From the simple shift ciphers used in the Roman empire to the complex enigma machine of World War II, The progression of code-breaking illustrates the innovativeness and perseverance inherent to human intellect.
One of the earliest known ciphers is the Polybius Square, a simple grid-based cipher that allowed messages to be encoded as pairs of numbers. An even simpler method, the Caesar Shift, involved shifting each letter in the plaintext a predetermined number down the alphabet to produce coded messages. These early techniques laid the groundwork for future code-breaking efforts and the development of more advanced cipher systems.
In this context, the Caesar Shift can be considered an early example of a cipher system. Here’s a quick example: using a Caesar Shift of three positions, the phrase “How Stuff Works” would be encoded as “Krz Vwxii Zrunv”. These early techniques laid the groundwork for future code-breaking efforts, teaching us the fundamental principles of encryption and decryption.
But code-breaking is not just about shifting letters and numbers. It’s also about understanding the patterns and frequencies of a language. This method of code breaking itself, known as frequency analysis, involves examining the frequency of letters in a given language to crack the coded message. For instance, in English, the most common letter is ‘E’. Hence, if your coded message has a high frequency of ‘Z’s, it’s likely that ‘Z’ corresponds to ‘E’ in your cipher. Such techniques have paved the way for the development of more sophisticated methods of code-breaking, including the use of machine learning and artificial intelligence in modern day cryptanalysis.
Room 40 The Admiralty, World War I Code Breaking
As technology progressed, so too did the complexity of ciphers and the machines used to create them. The advent of electricity and wireless telegraphy in the early 20th century allowed for more complex code creation and instantaneous two-way communication, which proved crucial during World War I.
During this time in the second world war, Britain’s code-breaking efforts were concentrated in a secretive unit known as Room 40. Here, British intelligence experts worked tirelessly to decipher German communications, which were enciphered using a modified version of the Playfair cipher. These decoding attempts played a key role in intercepting important communications., including the infamous Zimmermann Telegram, which ultimately brought the United States into the second world war.
Discover the faciniating history of Room 40 The Admiralty by reading our informative Article.
Enigma Code and World War II

During the early stages of World War II, code-breaking advanced significantly, with the introduction of the German Enigma machine. This sophisticated cipher machine was believed to be unbreakable, with its rotating wheels and complex settings creating an astronomical number of potential codes to break. However, the dedicated code-breakers at Bletchley Park in Britain rose to the challenge.
With the aid of a device known as the ‘bombe,’ the team at Bletchley Park was able to crack the Enigma code, a feat that is believed to have shortened the war by two to three years. This remarkable achievement was not the work of a single individual, but a collective war effort, that included the brilliant minds of mathematicians, linguists, and engineers.
Their contribution was not only pivotal to the Allied victory but also established a strong foundation for the evolution of modern computers and cryptography.
Alan Turing: A Brilliant Mathematician

Among the code-breakers at Bletchley Park, one figure stands out: Alan Turing. A brilliant mathematician, Turing made significant contributions to the field of code-breaking, and his work on deciphering the Enigma code played a key role in the Allied victory.
Turing’s most notable contributions include:
The creation of the Bombe machine, which automated the code-breaking process and substantially accelerated the decryption of Enigma messages
The development of a method known as ‘Turingery’
Authoring papers that discussed mathematical methods for code-breaking, providing a systematic approach to decrypting complex ciphers
His work laid the foundation for modern day cryptanalysis, and his legacy continues to inspire code-breakers and mathematicians today.
Colossus: The First Electronic Computer
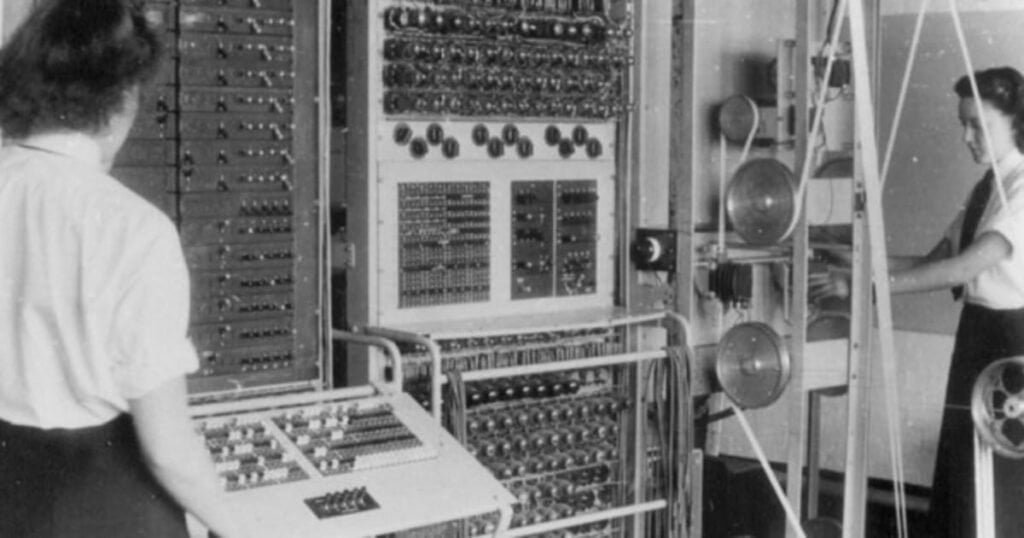
While Turing and his team were busy cracking the Enigma code, another group of code-breakers at Bletchley Park were working on an even bigger challenge: the Lorenz cipher, used by the German High Command. To crack this code, they developed the Colossus, often considered the first electronic computer.
The Colossus was designed to:
Decipher the ciphering system produced by the Lorenz SZ40/42 machine
Explore millions of possibilities to crack the code
Break the Lorenz cipher in a matter of hours
Provide crucial intelligence that contributed to the Allied victory in World War II
Evolution of Cipher Systems and Machines
The progressive journey from the straightforward shift ciphers of ancient Rome to the intricate machines of World War II signifies the inventiveness and resourcefulness of code-makers over the centuries. The Alberti Disc, invented by Leon Battista Alberti in the 15th century, is considered one of the earliest cipher devices.
Its design and use revolutionised cryptography during that time. This device operated through the interaction of two discs, one with a jumbled alphabet and the other with a second alphabet and the numbers 1 to 4. By rotating the outer disc, different letters were aligned with those on the inner circle, which were then used as plaintext.
Meanwhile, on the other side of the Atlantic, Thomas Jefferson was also making significant contributions to the field of code-making. He proposed a design for a ciphering machine that utilized a cylinder of discs mounted on a spindle, each disc containing the alphabet arranged in a random sequence.
To encrypt a message, the discs were aligned to spell out the message, and another gibberish row across the cylinder served as the encrypted text. These early machines laid the groundwork for the more complex cipher machines of the 20th century, including the Enigma machine and the Colossus.
Cryptanalysis: The Science of Breaking Codes
Cryptanalysis, or the art of code-breaking, extends beyond merely shifting letters and numbers. It also encompasses the comprehension of language patterns and frequencies, which is used to decrypt coded messages. This method, known as frequency analysis, involves examining the frequency of letters in a given language. As mentioned earlier, in English, the most common letter is ‘E’. Hence, if your coded message has a high frequency of ‘Z’s, it’s likely that the letter ‘Z’ corresponds to ‘E’ in your cipher.
The frequency analysis is just one tool in the cryptanalyst’s toolbox. They also employ a variety of methods, including cryptanalysis, called frequency analysis, and decryption based on frequency patterns. Pattern recognition, for instance, plays a crucial role in cryptanalysis by facilitating the identification of repetitive sequences or patterns within encrypted messages. These patterns may reveal common words or letter pairings, enabling cryptanalysts to identify weaknesses within the encryption of following message and ultimately make it easier to decipher.
Aside problem solving skills, from understanding language patterns, letters and frequencies, code-breaking also demands specific mental attributes such as:
patience
perseverance
meticulous analysis
resilience to overcome numerous unsuccessful attempts before arriving at a successful solution
It’s a field that requires both the mind of a scientist and the soul of a detective, making it one of the most challenging and rewarding fields of study.
Notable Unsolved Codes and Mysteries
In spite of significant advancements in code-breaking, numerous notable unsolved secret codes and mysteries persist, confounding experts. These include the Beale treasure, the Zodiac killer’s ciphers, and the Voynich Manuscript. Each of these own codes presents unique challenges and has resisted all attempts at decryption, serving as a reminder of the complexity and ingenuity of code-makers throughout history.
The Beale treasure, for instance, is reputedly a hidden fortune attributed to a man named Beale, accompanied by a cryptic message indicating its whereabouts. Despite the efforts of countless treasure hunters and cryptanalysts, the location of the Beale treasure remains a mystery to this day. Similarly, the Zodiac killer’s ciphers, a set of encrypted messages sent to the media by a serial murderer in the late 1960s, have remained largely unsolved, adding to the mystery and terror of the Zodiac case.
Perhaps the most intriguing of all is the Voynich Manuscript, a 15th-century book written in an unknown script and filled with mysterious illustrations. Despite the efforts of countless cryptanalysts, including some of the most famous code-breakers from both World Wars, the Voynich Manuscript has remained undeciphered, making it one of the most famous unsolved codes in history. These unsolved mysteries serve as a testament to the complexity of codes, and a challenge to future generations of code-breakers.
The Role of Code Breaking in Modern Intelligence
Code-breaking holds a significant role in the domain of intelligence and espionage. It allows governments to intercept and decipher enemy communications, providing vital information that can influence the outcome of conflicts. In fact, modern intelligence agencies, such as the National Security Agency in the United States, were founded with code-breaking as one of their primary functions, including the deciphering of government code.
But the role of code-breaking in modern intelligence is not just limited to military and espionage activities. It’s also crucial in the fight against cybercrime, where hackers often use encryption to hide their activities. Cryptography, the science of creating codes, is now a vital tool in protecting sensitive information and securing digital communications.
As we move further into the digital age, the role of code-breaking in modern intelligence will only become more important, highlighting the need for skilled cryptanalysts in both public and private sectors.
Code Breaking and the Future – AI & Quantum Computing
As we envision the future, code-breaking’s role in society is poised to evolve alongside the emergence of artificial intelligence and quantum computing. These emerging technologies have the potential to revolutionise the field of cryptanalysis, offering new tools and techniques for breaking codes and deciphering encrypted messages.

Artificial Intelligence, for instance, has the potential to automate the process of cryptanalysis, using algorithms and machine learning to recognise patterns and decipher codes more quickly and accurately than human analysts.
On the other hand, Quantum computing, with its potential to perform calculations at speeds unimaginable with today’s computers, could potentially crack even the most complex encryption algorithms, posing a significant challenge to the security of digital communications.
However, the precise impact of these technologies on the field of code-breaking is still a topic of ongoing research, and it’s clear that the next generation of code-breakers will need to be well-versed in these new technologies.
Developing Code Breaking Skills
For those captivated by code-breaking and aspiring to develop their own skills, several approaches can be taken. Code-breaking requires:
A robust understanding of mathematics
Efficient collaboration and communication
Familiarity with various languages
Problem-solving abilities
Meticulous attention to detail
These skills can be developed through practice and study, and there are numerous resources available online to help you get started.
In addition to understanding the theory, developing your code-breaking skills also requires practice. This can involve testing your problem-solving capabilities, attempting to decipher secret messages and code messages using clues, and using interactive web applications such as Code Break.
Patience and persistence are key, as the process of breaking a code can often be a lengthy and painstaking process. But with enough practice, anyone can learn to crack codes and unlock the secrets they hold.
Educational Resources and Activities
For those keen on delving deeper into code-breaking, an array of educational resources and activities are readily available. The School Code Breaking website from the British International School Phuket, for example, offers a wealth of information and activities aimed at teaching the principles of code-breaking, including British code breaking, to students of all ages.
This includes interactive puzzles and challenges, as well as resources for teachers looking to incorporate code-breaking into their curriculum. In addition to online resources, there are also a number of books that offer in-depth explorations of the world of code-breaking. Notable titles include:
‘The Codebreakers’ by David Kahn
‘The Woman Who Smashed Codes: A True Story of Love, Spies, and the Unlikely Heroine who Outwitted America’s Enemies’ by Jason Fagone
‘The Code Book’ by Simon Singh
These books offer a comprehensive overview of the history and principles of code-breaking, making them a valuable resource for anyone interested in writing in this fascinating field.
Code Breaking in Popular Culture
Code-breaking is not limited to the realms of academia and intelligence agencies. It has permeated popular culture, where it has been romanticised and dramatised in various forms of media such as movies, books, and television shows. From the cryptic clues in “The Da Vinci Code,” to the dramatic portrayals of World War II code breakers in “The Imitation Game,” the fascination with the work of a code breaker has captured the public’s imagination and sparked interest in this intriguing field.
While these portrayals are often dramatised and not always accurate, they do highlight the intrigue and mystery associated with code-breaking. They also serve to introduce a broader audience to the principles of cryptography, and inspire a new generation of code-breakers. Whether it’s the code-breaking efforts of the Bletchley Park team in “The Imitation Game,” for example, or the cryptic messages of the Zodiac killer in the movie “Zodiac,” these popular culture representations continue to fuel interest in the art of code-breaking.
Summary
From ancient ciphers to modern computer encryption algorithms, the world of code-breaking is a field of study that spans centuries and encompasses myriad disciplines. It’s a field that requires a keen mind, an eye for patterns, and a deep understanding of language, mathematics, and technology. As we’ve explored in this blog post, code-breaking has played a crucial role in shaping the course of history, and continues to play a vital role in our modern world.
As we look to the future, it’s clear that the field of code-breaking will continue to evolve, with emerging technologies such as artificial intelligence and quantum computing offering new challenges and opportunities. Whether you’re a budding cryptanalyst, a history enthusiast, or simply intrigued by the world of codes and ciphers, we hope this blog post has sparked your interest and deepened your understanding of this fascinating field.
Frequently Asked Questions
What is the code breaking technique?
The code breaking technique often involves methods such as frequency analysis, which uses the most common letters of a language or alphabet to begin deciphering, such as starting with the letter ‘e’ in English. Al Kindi was one of the early figures behind this decryption method.
How did code breaking work in WW2?
Code breaking in WW2 worked through the use of machines like the Enigma, which allowed operators to encrypt messages using a letter substitution system and variable rotors, and message recipients needed to know the exact settings to decode the message.
Who invented code-breaking?
Alan Turing, a British mathematician, invented code-breaking, including the secret development of the WWII Bombe machine to decrypt messages sent by German Enigma cipher machines and a complex code-breaking technique called “Turingery”.
What is the Enigma machine?
The Enigma machine was a complex cipher machine used by the Germans during World War II and was eventually cracked by the code-breakers at Bletchley Park.
What role does code-breaking play in modern intelligence?
Code-breaking plays a crucial role in modern intelligence gathering, as it allows governments to intercept and decipher enemy communications and combat cybercrime by uncovering hidden illegal activities.
What does code breaking mean?
coded or encrypted messages without having access to the secret information (usually called a key) that is normally required to do so. The goal of code breaking is to interpret the message and understand its contents without the consent or knowledge of the sender.
What is the code breaking activity?
Code breaking activity refers to the process and practice of deciphering coded or encrypted messages without the original key intended for its decryption. This activity is a fundamental aspect of cryptanalysis, which is a branch of cryptology. Cryptology encompasses both the creation of codes and ciphers (cryptography) and their decryption (cryptanalysis).
What is the study of code breaking?
The study of code breaking is known as “cryptanalysis.” It is a branch of cryptology, which encompasses both the creation of codes and ciphers (cryptography) and their breaking (cryptanalysis). Cryptanalysis involves the science and art of deciphering coded or encrypted messages without the original key or method used to encode the message. This field combines aspects of mathematics, computer science, linguistics, and even psychology.
What are code breaking puzzles
Code breaking puzzles are a form of mental challenge or game that involve deciphering a coded message or solving a cryptographic problem. These puzzles mimic the basic principles of cryptanalysis but are typically designed for entertainment, education, or intellectual challenge rather than for real-world espionage or data security. They range from simple substitution ciphers to more complex cryptographic riddles.
Useful Reference Websites
- GCHQ (Government Communications Headquarters) – www.gchq.gov.uk
- The UK’s intelligence and security organization, successor to the Government Code and Cypher School, which operated Bletchley Park during World War II.
- Bletchley Park – www.bletchleypark.org.uk
- The historic site of British codebreaking activities during World War II, now a museum offering extensive resources on the history of code breaking.
- The National Archives – www.nationalarchives.gov.uk
- Offers a wealth of historical documents and records, including those related to British intelligence and code-breaking efforts.
- Imperial War Museums – www.iwm.org.uk
- Covers a wide range of topics related to British and Commonwealth military history, including intelligence and code-breaking.
- BBC History – www.bbc.co.uk/history
- Provides accessible articles and resources on various historical topics, including wartime intelligence and cryptography.
- National Security Agency (NSA) – www.nsa.gov
- The official site of the NSA, offering historical insights into American code-breaking and cryptologic history.
- CIA (Central Intelligence Agency) – www.cia.gov
- Features a history section with information on intelligence and code-breaking operations in the USA.
- American Cryptogram Association – www.cryptogram.org
- A resource for enthusiasts of cryptology, offering insights into the art and science of code breaking.
- Cryptologic Museum – www.nsa.gov/about/cryptologic-heritage/museum
- Operated by the NSA, this museum offers a historical perspective on American cryptology.
- Smithsonian Magazine – www.smithsonianmag.com
- Offers articles and stories on a variety of topics, including historical pieces on code breaking and intelligence.
With over three decades of experience in the heart of London’s financial sector, I have dedicated my career to the pursuit of robust cybersecurity practices and IT leadership. As a Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Chief Information Security Officer (C|CISO), Certified Ethical Hacker (CEH), and Computer Hacking Forensic Investigator (CHFI), I bring a wealth of knowledge and expertise to the table.
My journey in the field of cybersecurity has not only been about personal growth but also about sharing my insights with others. As an international speaker, I have had the privilege of addressing audiences worldwide, discussing the importance of cybersecurity in today’s digital age. My passion for knowledge sharing extends to my work as an author and blogger, where I delve into the complexities of cybersecurity, offering practical advice and thought leadership.
In my role as a CISO and Head of IT, I have overseen the development and implementation of comprehensive information security and IT strategies. My focus has always been on creating resilient systems capable of withstanding the evolving landscape of cyber threats.
My Master’s degree in Cybersecurity has provided a solid academic foundation, which, when combined with my practical experience, allows me to approach cybersecurity from a holistic perspective.
I am always open to connecting with other professionals in the field, sharing knowledge, and exploring new opportunities. Let’s secure the digital world together.

